Cisco CCNA Security 210-260 dumps exam preparation kit contains all the necessary 210-260 questions that you need to know. High quality Cisco CCNA Security 210-260 dumps vce youtube demo update free shared. “Implementing Cisco Network Security” is the name of Cisco CCNA Collaboration https://www.leads4pass.com/210-065.html exam dumps which covers all the knowledge points of the real Cisco exam. 210-260 IINS – Cisco 100% success and guarantee to pass Cisco 210-065 exam.
Latest Cisco 210-260 dumps pdf training resource: https://drive.google.com/open?id=0B_7qiYkH83VRcnI0SE83bHBvQ1k
Latest Cisco 210-060 dumps pdf training resource: https://drive.google.com/open?id=0B_7qiYkH83VRSHJTTV9NMjQ0dmc
Vendor: Cisco
Certifications: CCNA Security
Exam Name: Implementing Cisco Network Security
Exam Code: 210-260
Total Questions: 329 Q&As
Prepare for Cisco 210-260 exam with best Cisco CCNA Security 210-260 dumps pdf study guides and materials online download free try from leads4pass. Free latest Cisco 210-260 dumps pdf practice materials and youtube demo. The best useful Cisco CCNA Security 210-260 dumps vce software update download free try.
2018 New Cisco CCNA Security 210-260 Dumps Exam Questions And Answers (Q11-Q30)
QUESTION 11
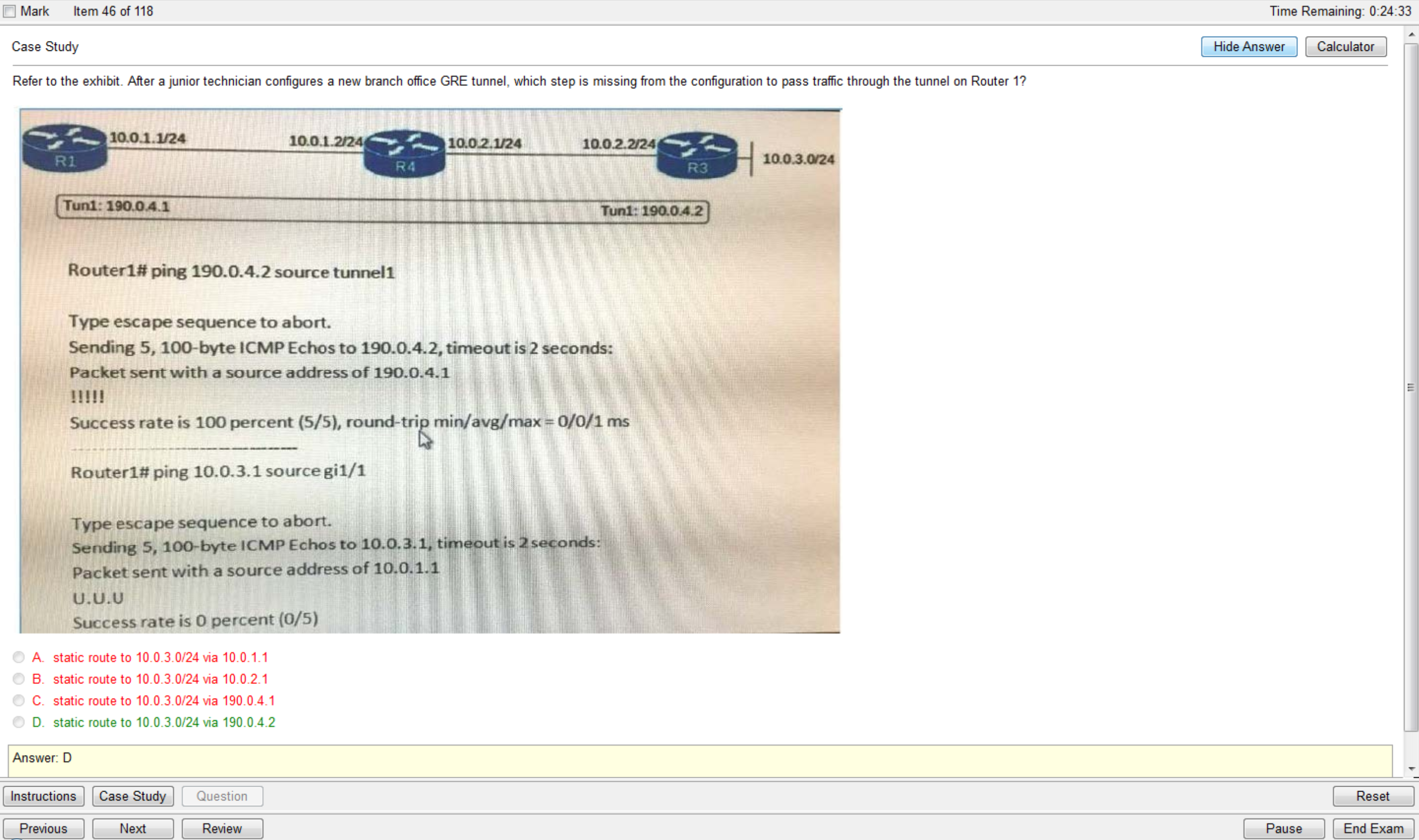
Refer to the exhibit.
If a supplicant supplies incorrect credentials for all authentication methods configured on the switch, how will the switch respond?
A. The supplicant will fail to advance beyond the webauth method.
B. The switch will cycle through the configured authentication methods indefinitely.
C. The authentication attempt will time out and the switch will place the port into the unauthorized state.
D. The authentication attempt will time out and the switch will place the port into VLAN 101.
Correct Answer: A
QUESTION 12
What configure mode you used for the command ip ospf authentication-key c1$c0?
A. global
B. privileged
C. in-line
D. Interface
Correct Answer: D
Explanation:
ip ospf authentication-key is used under interface configuration mode, so it’s in interface level, under global configuration mode. If it asks about interface level then choose that.
interface Serial0
ip address 192.16.64.1 255.255.25
QUESTION 13
Which two features are commonly used CoPP and CPPr to protect the control plane? (Choose two.)
A. QoS
B. traffic classification
C. access lists
D. policy maps
E. class maps
F. Cisco Express Forwarding
Correct Answer: AB
QUESTION 14
What is one requirement for locking a wired or wireless device from ISE?
A. The ISE agent must be installed on the device.
B. The device must be connected to the network when the lock command is executed.
C. The user must approve the locking action.
D. The organization must implement an acceptable use policy allowing device locking.
Correct Answer: A
QUESTION 15
Which three statements are characteristics of DHCP Spoofing? (choose three)
A. Arp Poisoning
B. Modify Traffic in transit
C. Used to perform man-in-the-middle attack
D. Physically modify the network gateway
E. Protect the identity of the attacker by masking the DHCP address
F. can access most network devices
Correct Answer: ABC
QUESTION 16
Which statement correctly describes the function of a private VLAN?
A. A private VLAN partitions the Layer 2 broadcast domain of a VLAN into subdomains
B. A private VLAN partitions the Layer 3 broadcast domain of a VLAN into subdomains
C. A private VLAN enables the creation of multiple VLANs using one broadcast domain
D. A private VLAN combines the Layer 2 broadcast domains of many VLANs into one major broadcast domain
Correct Answer: A
QUESTION 17
which feature allow from dynamic NAT pool to choose next IP address and not a port on a used IP address? 210-260 dumps
A. next IP
B. round robin
C. Dynamic rotation
D. Dynamic PAT rotation
Correct Answer: B
QUESTION 18
Which type of encryption technology has the broadcast platform support?
A. Middleware
B. Hardware
C. Software
D. File-level
Correct Answer: C
QUESTION 19
When an IPS detects an attack, which action can the IPS take to prevent the attack from spreading?
A. Deny the connection inline.
B. Perform a Layer 6 reset.
C. Deploy an antimalware system.
D. Enable bypass mode.
Correct Answer: A
QUESTION 20
Which four tasks are required when you configure Cisco IOS IPS using the Cisco Configuration Professional IPS wizard? (Choose four.)
A. Select the interface(s) to apply the IPS rule.
B. Select the traffic flow direction that should be applied by the IPS rule.
C. Add or remove IPS alerts actions based on the risk rating.
D. Specify the signature file and the Cisco public key.
E. Select the IPS bypass mode (fail-open or fail-close).
F. Specify the configuration location and select the category of signatures to be applied to the selected interface(s).
Correct Answer: ABDF
Explanation:
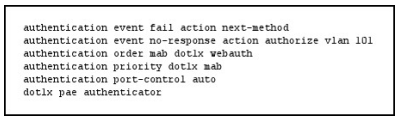
Step 11. At the `Select Interfaces’ screen, select the interface and the direction that IOS IPS will be applied to, then click `Next’ to continue.
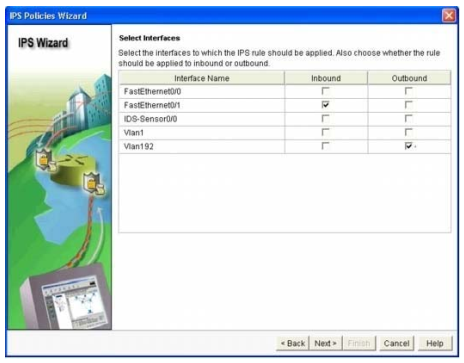
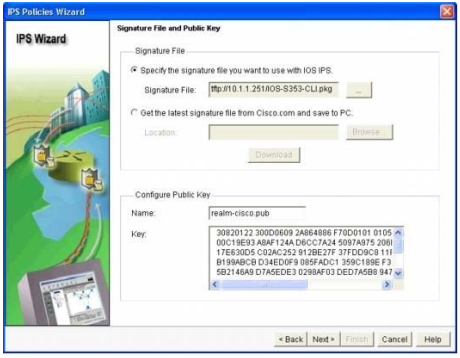
Step 12. At the `IPS Policies Wizard’ screen, in the `Signature File’ section, select the first radio button “Specify the signature file you want to use with IOS IPS”, then click the “…” button to bring up a dialog box to specify the location of the signature package file, which will be the directory specified in Step 6. In this example, we use tftp to download the signature package to the router.
Step 13. In the `Configure Public Key’ section, enter `realm-cisco.pub’ in the `Name’ text field, then copy and paste the following public key’s key-string in the `Key’ text field. This public key can be downloaded from Cisco.com.
30820122 300D0609 2A864886 F70D0101 01050003 82010F00 3082010A 02820101 00C19E93 A8AF124A D6CC7A24 5097A975 206BE3A2 06FBA13F 6F12CB5B 4E441F16 17E630D5 C02AC252 912BE27F 37FDD9C8 11FC7AF7
DCDD81D9 43CDABC3 6007D128
B199ABCB D34ED0F9 085FADC1 359C189E F30AF10A C0EFB624 7E0764BF 3E53053E
5B2146A9 D7A5EDE3 0298AF03 DED7A5B8 9479039D 20F30663 9AC64B93 C0112A35 FE3F0C87 89BCB7BB 994AE74C FA9E481D F65875D6 85EAF974 6D9CC8E3 F0B08B85
50437722 FFBE85B9 5E4189FF CC189CB9 69C46F9C A84DFBA5 7A0AF99E AD768C36
006CF498 079F88F8 A3B3FB1F 9FB7B3CB 5539E1D1 9693CCBB 551F78D2 892356AE 2F56D826 8918EF3C 80CA4F4D 87BFCA3B BFF668E9 689782A5 CF31CB6E B4B094D3
F3020301 0001
QUESTION 21
Which ports need to be active for AAA server and a Microsoft server to permit Active Directory authentication?
A. 445 and 389
B. 888 and 3389
C. 636 and 4445
D. 363 and 983
Correct Answer: A
QUESTION 22
DRAG DROP
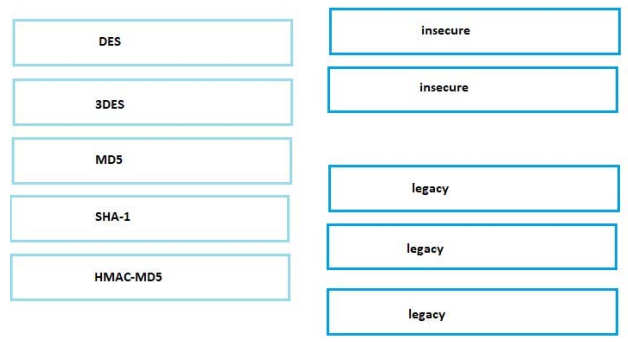
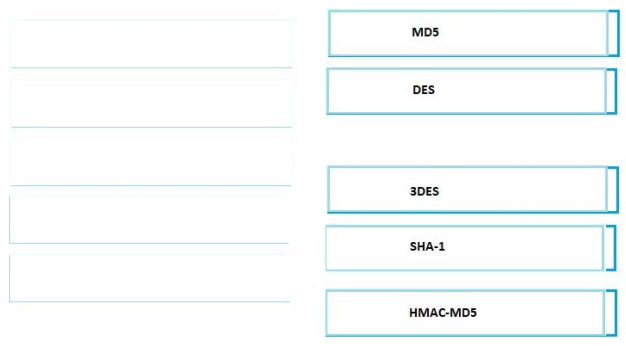
Drag the hash or algorithm from the left column to its appropriate category on the right.
Select and Place:
Correct Answer:
QUESTION 23
If a switch receives a superior BPDU and goes directly into a blocked state, what mechanism must be in use?
A. root guard
B. EtherChannel guard
C. loop guard
D. BPDU guard
Correct Answer: A
QUESTION 24
Which two are valid types of VLANs using PVLANs? (Choose two.)
A. Backup VLAN
B. Secondary VLAN
C. Promiscuous VLAN
D. Community VLAN
E. Isolated VLAN
Correct Answer: DE
QUESTION 25
Which two are the default settings for port security? 210-260 dumps (Choose two.)
A. Violation is Protect
B. Maximum number of MAC addresses is 1
C. Violation is Restrict
D. Violation is Shutdown
E. Maximum number of MAC addresses is 2
Correct Answer: BD
QUESTION 26
Refer to the exhibit.
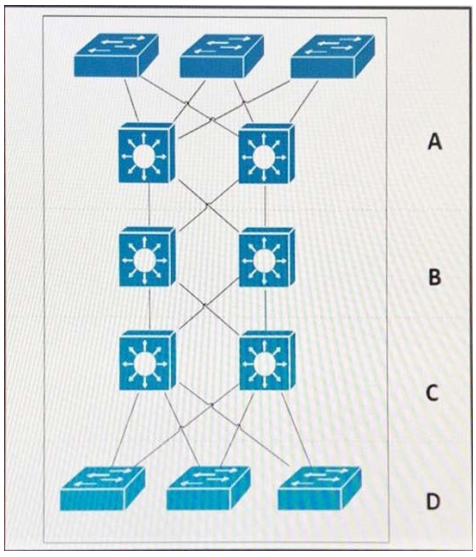
Which area represents the data center?
A. A
B. B
C. C
D. D
Correct Answer: A
QUESTION 27
Refer to the exhibit.
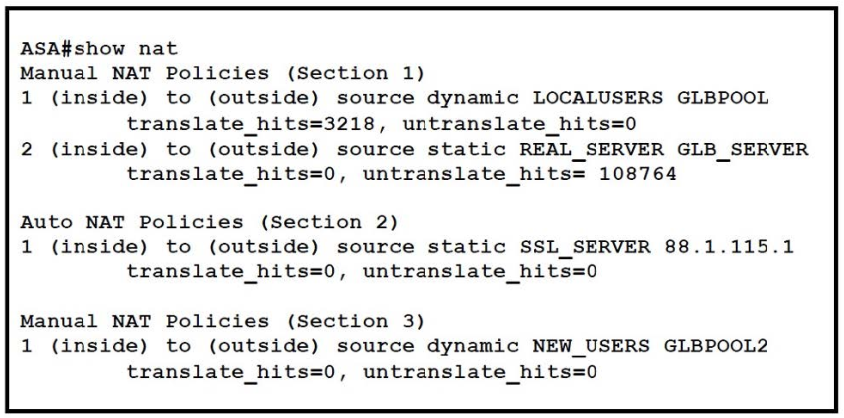
A network security administrator checks the ASA firewall NAT policy table with the show nat command.
Which statement is false?
A. First policy in the Section 1 is dynamic nat entry defined in the object configuration.
B. There are only reverse translation matches for the REAL_SERVER object.
C. NAT policy in Section 2 is a static entry defined in the object configuration.
D. Translation in Section 3 is used when a connection does not match any entries in first two sections.
Correct Answer: D
QUESTION 28
Which two are characteristics of RADIUS? (Choose two.)
A. Uses TCP ports 1812/1813
B. Uses UDP port 49
C. Encrypts only the password between user and server
D. Uses TCP port 49
E. Uses UDP ports 1812/1813
Correct Answer: CE
QUESTION 29
Which two types of firewalls work at layer 4 and above? (Choose two.)
A. Application level firewall
B. Circuit-level gateway
C. Static packet filter
D. Network Address Translation
E. Stateful inspection
Correct Answer: AB
QUESTION 30
When setting up a site-to-site VPN with PSK authentication on a Cisco router, which two elements must be configured under crypto map? (Choose two.)
A. nat
B. peer
C. pfs
D. reverse-route
E. transform-set
Correct Answer: BE
Get your Cisco CCNA Security 210-260 dumps exam preparation questions in form of 210-260 PDF. Useful Cisco CCNA Security https://www.leads4pass.com/210-260.html dumps pdf training resources which are the best for clearing 210-260 exam test, and to get certified by Cisco CCNA Security. 100% passing guarantee and full refund in case of failure.
Best Cisco CCNA Security 210-260 dumps vce youtube: https://youtu.be/QuJdf0nvAMg