
How do I pass the Microsoft Azure Security Technologies AZ-500 certification exam? Examsall shares the latest and effective Microsoft AZ-500 exam questions and answers, online practice tests, and the most authoritative Microsoft exam experts update AZ-500 exam questions throughout the year. Get the full AZ-500 exam dumps selection: https://www.leads4pass.com/az-500.html (142 Q&As). Pass the exam with ease!
Table of Contents:
- Latest Microsoft AZ-500 google drive
- Effective Microsoft AZ-500 exam practice questions
- Related AZ-500 Popular Exam resources
- leads4pass Year-round Discount Code
- What are the advantages of leads4pass?
Latest microsoft AZ-500 google drive
[PDF] Free Microsoft AZ-500 pdf dumps download from Google Drive: https://drive.google.com/open?id=1wmsYeyeykzlfx271VyQr0Fy-W8hqGt3F
Exam AZ-500: Microsoft Azure Security Technologies: https://docs.microsoft.com/en-us/learn/certifications/exams/az-500
Candidates for this exam are Microsoft Azure security engineers who implement security controls, maintain the security posture, manage identity and access, and protect data, applications, and networks. Candidates identify and remediate vulnerabilities by using a variety of security tools, implement threat protection, and respond to security incident escalations. As a Microsoft Azure security engineer, candidates often serve as part of a larger team dedicated to cloud-based management and security and may also secure hybrid environments as part of an end-to-end infrastructure.
Candidates for this exam should have strong skills in scripting and automation; a deep understanding of networking, virtualization, and cloud N-tier architecture; and a strong familiarity with cloud capabilities, Microsoft Azure products and services, and other Microsoft products and services.
Skills measured
NOTE: The bullets that appear below each of the skills measured in the document below are intended to illustrate how we are assessing that skill. This list is not definitive or exhaustive.
- Manage identity and access (20-25%)
- Implement platform protection (35-40%)
- Manage security operations (15-20%)
- Secure data and applications (30-35%)
Latest updates microsoft AZ-500 exam practice questions
QUESTION 1
You have an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named
contoso.com.
You plan to implement an application that will consist of the resources shown in the following table.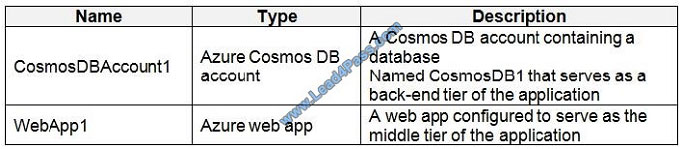
Users will authenticate by using their Azure AD user account and access the Cosmos DB account by using resource
tokens.
You need to identify which tasks will be implemented in CosmosDB1 and WebApp1.
Which task should you identify for each resource? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
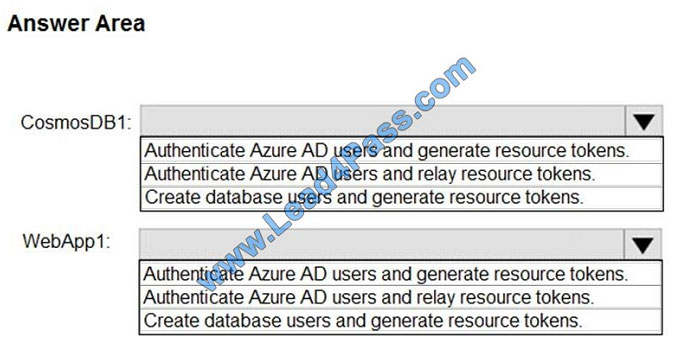
Correct Answer:
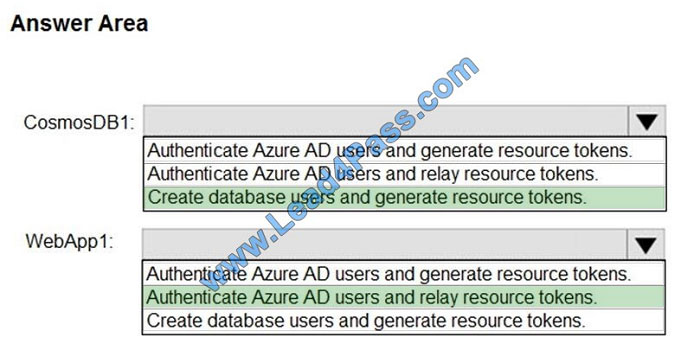
CosmosDB1: Create database users and generate resource tokens.
Azure Cosmos DB resource tokens provide a safe mechanism for allowing clients to read, write, and delete specific
resources in an Azure Cosmos DB account according to the granted permissions.
WebApp1: Authenticate Azure AD users and relay resource tokens
A typical approach to requesting, generating, and delivering resource tokens to a mobile application is to use a resource
token broker. The following diagram shows a high-level overview of how the sample application uses a resource token
broker to manage access to the document database data:
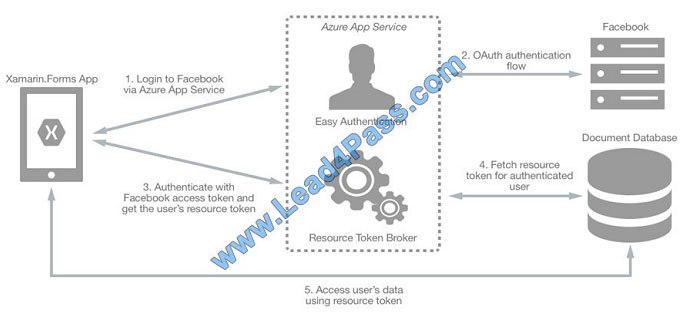
References: https://docs.microsoft.com/en-us/xamarin/xamarin-forms/data-cloud/cosmosdb/authentication
QUESTION 2
Your company uses Azure DevOps.
You need to recommend a method to validate whether the code meets the company\\’s quality standards and code
review standards.
What should you recommend implementing in Azure DevOps?
A. branch folders
B. branch permissions
C. branch policies
D. branch locking
Correct Answer: C
Branch policies help teams protect their important branches of development. Policies enforce your team\\’s code quality
and change management standards.
References: https://docs.microsoft.com/en-us/azure/devops/repos/git/branch-policies?view=azure-devopsandviewFallbackFrom=vsts
QUESTION 3
You need to ensure that User2 can implement PIM. What should you do first?
A. Assign User2 the Global administrator role.
B. Configure authentication methods for contoso.com.
C. Configure the identity secure score for contoso.com.
D. Enable multi-factor authentication (MFA) for User2.
Correct Answer: A
To start using PIM in your directory, you must first enable PIM.
1. Sign in to the Azure portal as a Global Administrator of your directory.
You must be a Global Administrator with an organizational account (for example, @yourdomain.com), not a Microsoft
account (for example, @outlook.com), to enable PIM for a directory.
Scenario: Technical requirements include: Enable Azure AD Privileged Identity Management (PIM) for contoso.com
References:
https://docs.microsoft.com/bs-latn-ba/azure/active-directory/privileged-identity-management/pim-getting-started
QUESTION 4
You plan to use Azure Log Analytics to collect logs from 200 servers that run Windows Server 2016.
You need to automate the deployment of the Microsoft Monitoring Agent to all the servers by using an Azure Resource
Manager template.
How should you complete the template? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:

QUESTION 5
Which virtual networks in Sub1 can User2 modify and delete in their current state? To answer, select the appropriate
options in the answer area. NOTE: Each correct selection is worth one point.
Hot Area: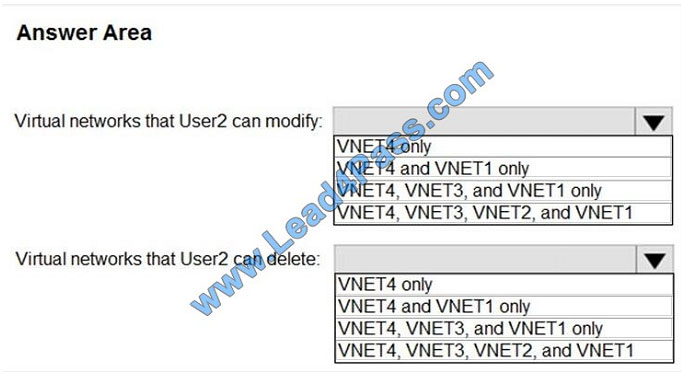
Correct Answer:
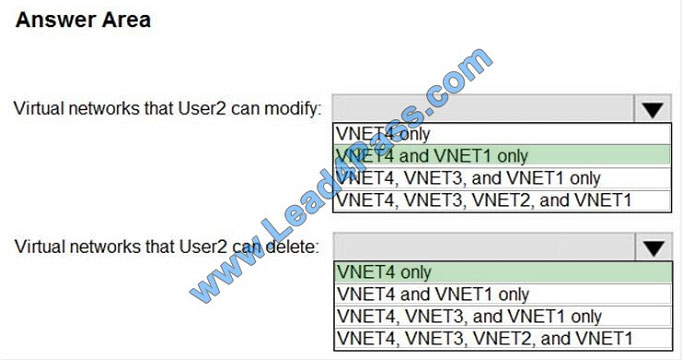
Box 1: VNET4 and VNET1 only
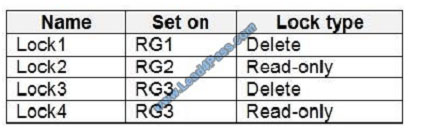
RG1 has only Delete lock, while there are no locks on RG4.
RG2 and RG3 both have Read-only locks.
Box 2: VNET4 only
AZ-500 Practice Test | AZ-500 Study Guide | AZ-500 Exam Questions 7 / 18https://www.leads4pass.com/az-500.html
2019 Latest leads4pass AZ-500 PDF and VCE dumps Download
There are no locks on RG4, while the other resource groups have either Delete or Read-only locks.
Note: As an administrator, you may need to lock a subscription, resource group, or resource to prevent other users in
your organization from accidentally deleting or modifying critical resources. You can set the lock level to CanNotDelete
or
ReadOnly. In the portal, the locks are called Delete and Read-only respectively.
CanNotDelete means authorized users can still read and modify a resource, but they can\\’t delete the resource.
ReadOnly means authorized users can read a resource, but they can\\’t delete or update the resource. Applying this
lock is similar to restricting all authorized users to the permissions granted by the Reader role.
Scenario:
User2 is a Security administrator.
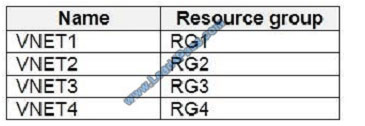
Sub1 contains six resource groups named RG1, RG2, RG3, RG4, RG5, and RG6.
User2 creates the virtual networks shown in the following table.
Sub1 contains the locks shown in the following table.
References: https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-group-lock-resources
QUESTION 6
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains
a unique solution that might meet the stated goals. Some question sets might have more than one correct solution,
while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not
appear in the review screen.
You have a hybrid configuration of Azure Active Directory (AzureAD).
You have an Azure HDInsight cluster on a virtual network.
You plan to allow users to authenticate to the cluster by using their on-premises Active Directory credentials.
You need to configure the environment to support the planned authentication.
Solution: You deploy the On-premises data gateway to the on-premises network.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
Instead, you connect HDInsight to your on-premises network by using Azure Virtual Networks and a VPN gateway.
Note: To allow HDInsight and resources in the joined network to communicate by name, you must perform the following
actions:
Create Azure Virtual Network.
Create a custom DNS server in the Azure Virtual Network.
Configure the virtual network to use the custom DNS server instead of the default Azure Recursive Resolver.
Configure forwarding between the custom DNS server and your on-premises DNS server.
References:
QUESTION 7
You are configuring an Azure Kubernetes Service (AKS) cluster that will connect to an Azure Container Registry.
You need to use the auto-generated service principal to authenticate to the Azure Container Registry.
What should you create?
A. an Azure Active Directory (Azure AD) group
B. an Azure Active Directory (Azure AD) role assignment
C. an Azure Active Directory (Azure AD) user
D. a secret in Azure Key Vault
Correct Answer: B
When you create an AKS cluster, Azure also creates a service principal to support cluster operability with other Azure
resources. You can use this auto-generated service principal for authentication with an ACR registry. To do so, you
need to create an Azure AD role assignment that grants the cluster\\’s service principal access to the container registry.
References: https://docs.microsoft.com/bs-latn-ba/azure/container-registry/container-registry-auth-aks
QUESTION 8
You have an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named
contoso.com.
You are assigned the Global administrator role for the tenant. You are responsible for managing Azure Security Center
settings.
You need to create a custom sensitivity label.
What should you do first?
A. Create a custom sensitive information type.
B. Elevate access for global administrators in Azure AD.
C. Upgrade the pricing tier of the Security Center to Standard.
D. Enable integration with Microsoft Cloud App Security.
Correct Answer: A
First, you need to create a new sensitive information type because you can\\’t directly modify the default rules.
References: https://docs.microsoft.com/en-us/office365/securitycompliance/customize-a-built-in-sensitive-information-type
QUESTION 9
You need to meet the identity and access requirements for Group1. What should you do?
A. Add a membership rule to Group1.
B. Delete Group1. Create a new group named Group1 that has a membership type of Office 365. Add users and
devices to the group.
C. Modify the membership rule of Group1.
D. Change the membership type of Group1 to Assigned. Create two groups that have dynamic memberships. Add the
new groups to Group1.
Correct Answer: B
Incorrect Answers:
A, C: You can create a dynamic group for devices or for users, but you can\\’t create a rule that contains both users and
devices.
D: For assigned group you can only add individual members.
Scenario:
Litware identifies the following identity and access requirements: All San Francisco users and their devices must be
members of Group1.
The tenant currently contain this group: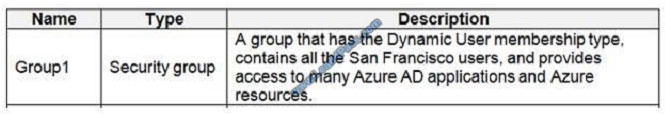
References: https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/groups-dynamic-membership
https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/active-directory-groups-create-azure-portal
QUESTION 10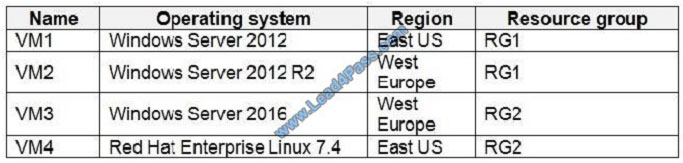
You create an Azure Log Analytics workspace named Analytics1 in RG1 in the East US region.
Which virtual machines can be enrolled in Analytics1?
A. VM1 only
B. VM1, VM2, and VM3 only
C. VM1, VM2, VM3, and VM4
D. VM1 and VM4 only
Correct Answer: A
Note: Create a workspace
In the Azure portal, click All services. In the list of resources, type Log Analytics. As you begin typing, the list filters
based on your input. Select Log Analytics.
Click Create, and then select choices for the following items:
Provide a name for the new Log Analytics workspace, such as DefaultLAWorkspace. OMS workspaces are now
referred to as Log Analytics workspaces.
Select a Subscription to link to by selecting from the drop-down list if the default selected is not appropriate.
For Resource Group, select an existing resource group that contains one or more Azure virtual machines.
Select the Location your VMs are deployed to. For additional information, see which regions Log Analytics is available
in.
Incorrect Answers:
B, C: A Log Analytics workspace provides a geographic location for data storage. VM2 and VM3 are at a different
location.
D: VM4 is a different resource group.
References: https://docs.microsoft.com/en-us/azure/azure-monitor/platform/manage-access
QUESTION 11
Your company has an Azure Active Directory (Azure AD) tenant named contoso.com.
The company is developing an application named App1. App1 will run as a service on server that runs Windows Server
2016. App1 will authenticate to contoso.com and access Microsoft Graph to read directory data.
You need to delegate the minimum required permissions to App1.
Which three actions should you perform in sequence from the Azure portal? To answer, move the appropriate actions
from the list of actions to the answer area and arrange them in the correct order.
Select and Place: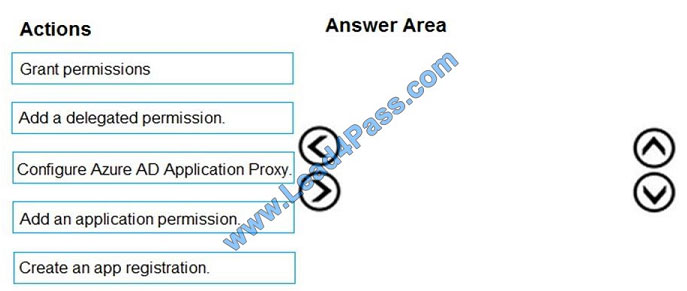
Correct Answer:
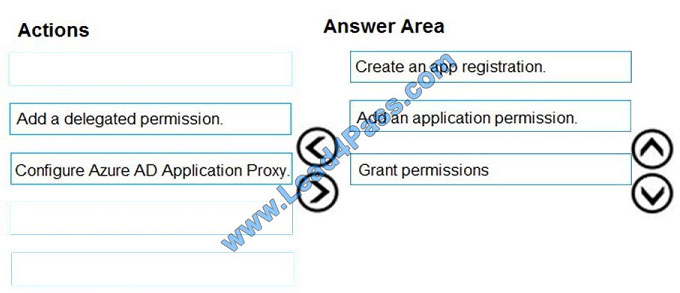
Step 1: Create an app registration
First the application must be created/registered.
Step 2: Add an application permission
Application permissions are used by apps that run without a signed-in user present.
Step 3: Grant permissions
Incorrect Answers:
Delegated permission
Delegated permissions are used by apps that have a signed-in user present.
Application Proxy:
Azure Active Directory\\’s Application Proxy provides secure remote access to on-premises web applications.
References:
https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-permissions-and-consent
QUESTION 12
You have an Azure subscription that contains the virtual machines shown in the following table.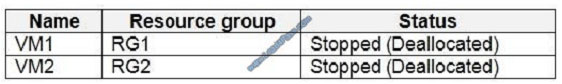
You create the Azure policies shown in the following table.
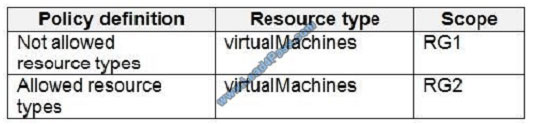
You create the resource locks shown in the following table.
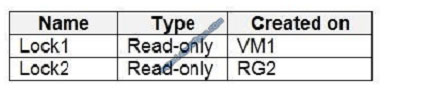
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct
selection is worth one point.
Hot Area:
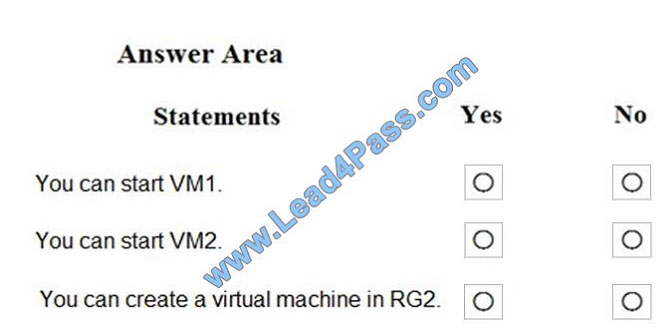
Correct Answer:
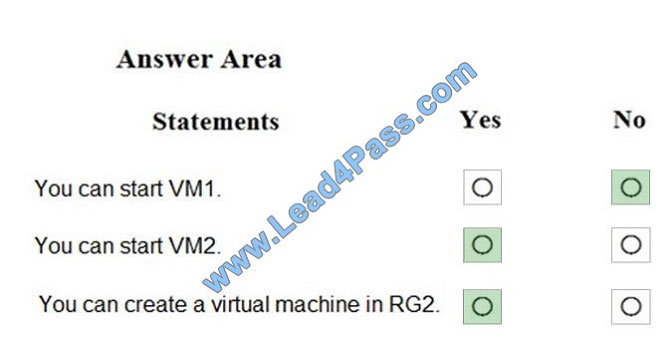
References: https://docs.microsoft.com/en-us/azure/governance/blueprints/concepts/resource-locking
QUESTION 13
You have Azure virtual machines that have Update Management enabled. The virtual machines are configured as
shown in the following table.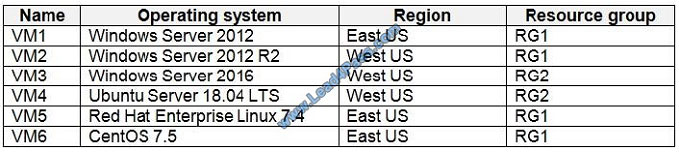
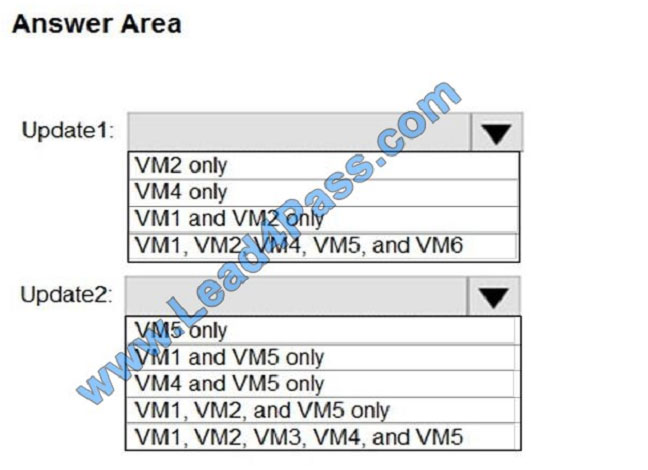
You schedule two update deployments named Update1 and Update2. Update1 updates VM3. Update2 updates VM6.
Which additional virtual machines can be updated by using Update1 and Update2? To answer, select the appropriate
options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
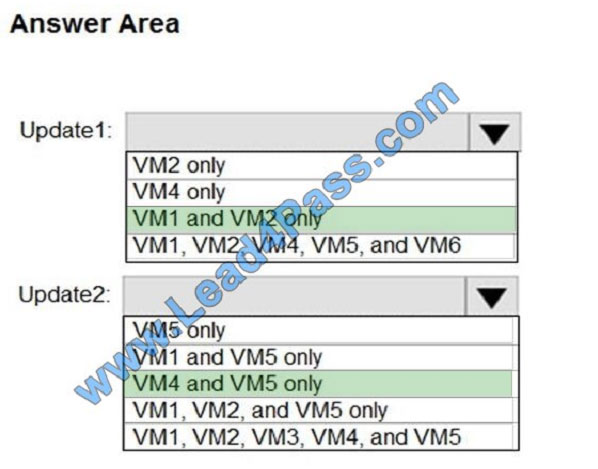
Update1: VM1 and VM2 only
VM3: Windows Server 2016 West US RG2
Update2: VM4 and VM5 only
VM6: CentOS 7.5 East US RG1
For Linux, the machine must have access to an update repository. The update repository can be private or public.
References: https://docs.microsoft.com/en-us/azure/automation/automation-update-management
Related Microsoft AZ-500 Popular Exam resources
| title | youtube | microsoft | leads4pass | leads4pass Total Questions | |
|---|---|---|---|---|---|
| Microsoft Azure | leads4pass AZ-500 dumps pdf | leads4pass AZ-500 youtube | Microsoft Azure Security Technologies | https://www.leads4pass.com/az-500.html | 142 Q&A |
leads4pass Year-round Discount Code

What are the advantages of leads4pass?
leads4pass employs the most authoritative exams from Microsoft, Cisco, CompTIA, Oracle, LPI, etc. We update exam data throughout the year. Highest pass rate! We have a large user base. We are an industry leader!
Choose leads4pass to pass the exam with ease!

Summarize:
It’s not easy to pass the Microsoft AZ-500 exam, but with accurate learning materials and proper practice, you can crack the exam with excellent results. https://www.leads4pass.com/az-500.html provides you with the most relevant learning materials that you can use to help you prepare.