leads4pass has updated CompTIA SY0-501 dumps issues! The latest SY0-501 exam questions can help you pass the exam! All questions are corrected to ensure authenticity and effectiveness! Download the leads4pass SY0-501 VCE dumps or PDF dumps: https://www.leads4pass.com/sy0-501.html (Total Questions: 1139 Q&A SY0-501 Dumps)
Examsall Exam Table of Contents:
- Latest CompTIA SY0-501 google drive
- Effective CompTIA SY0-501 Practice testing questions
- leads4pass Year-round Discount Code
- What are the advantages of leads4pass?
Latest CompTIA SY0-501 google drive
[Latest PDF] Free CompTIA SY0-501 pdf dumps download from Google Drive: https://drive.google.com/file/d/1xQJKwWVvk_za8X5PTP1GorNuYmFyE039/
Latest updates CompTIA SY0-501 exam practice questions
QUESTION 1
A forensic analyst is asked to respond to an ongoing network attack on a server. Place the items in the list below in the
correct order in which the forensic analyst should preserve them.
Select and Place: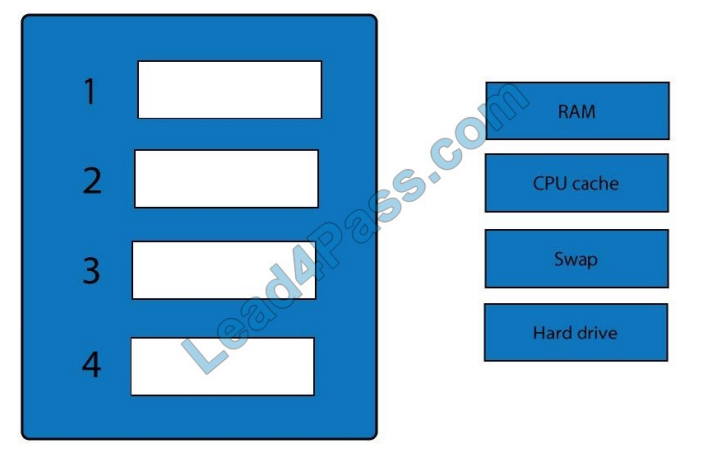
Correct Answer: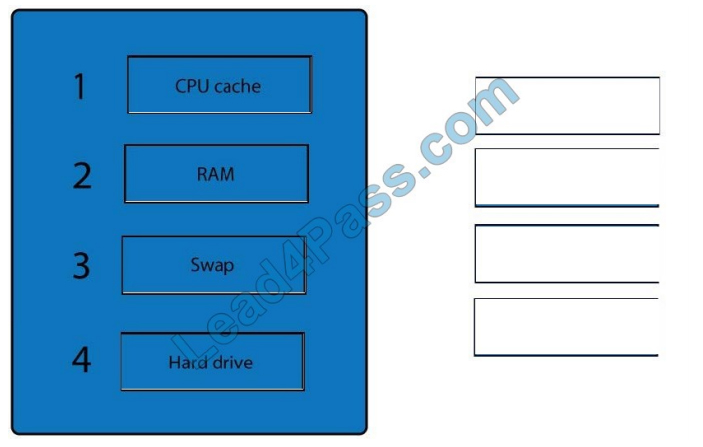
When dealing with multiple issues, address them in order of volatility (OOV); always deal with the most volatile first.
Volatility can be thought of as the amount of time that you have to collect certain data before a window of opportunity is
gone.
Naturally, in an investigation, you want to collect everything, but some data will exist longer than others, and you cannot
possibly collect all of it once. As an example, the OOV in an investigation may be RAM, hard drive data, CDs/DVDs,
and
printouts.
Order of volatility: Capture system images as a snapshot of what exists, look at network traffic and logs, capture any
relevant video/screenshots/hashes, record time offset on the systems, talk to witnesses and track total man-hours and
expenses associated with the investigation.
References:
Dulaney, Emmett and Chuck Easton, CompTIA Security+ Study Guide, 6th Edition, Sybex, Indianapolis, 2014, p. 453
QUESTION 2
A forensic analyst is asked to respond to an ongoing network attack on a server. Place the items in the list below in the
correct order in which the forensic analyst should preserve them.
Select and Place: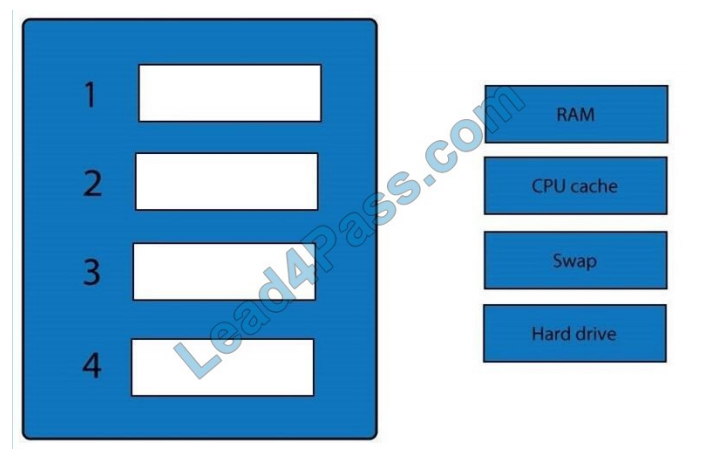
Correct Answer
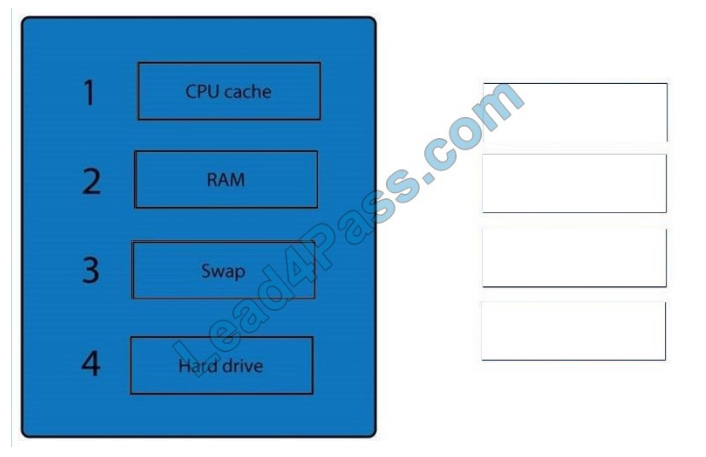
When dealing with multiple issues, address them in order of volatility (OOV); always deal with the most volatile first.
Volatility can be thought of as the amount of time that you have to collect certain data before a window of opportunity is
gone.
Naturally, in an investigation, you want to collect everything, but some data will exist longer than others, and you cannot
possibly collect all of it once. As an example, the OOV in an investigation may be RAM, hard drive data, CDs/DVDs,
and
printouts.
Order of volatility: Capture system images as a snapshot of what exists, look at network traffic and logs, capture any
relevant video/screenshots/hashes, record time offset on the systems, talk to witnesses and track total man-hours and
expenses associated with the investigation.
QUESTION 3
After reports of slow internet connectivity, a technician reviews the following logs from a server\\’s host-based firewall:
Which of the following can the technician conclude after reviewing the above logs?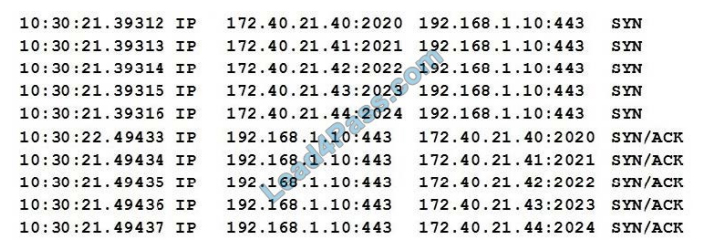
A. The server is under a DDoS attack from multiple geographic locations.
B. The server is compromised and is attacking multiple hosts on the Internet.
C. The server is under an IP spoofing resource exhaustion attack.
D. The server is unable to complete the TCP three-way handshake and send the last ACK.
Correct Answer: C
QUESTION 4
A security consultant discovers that an organization is using the PCL protocol to print documents, utilizing the default
driver and print settings. Which of the following is the MOST likely risk in this situation?
A. An attacker can access and change the printer configuration.
B. SNMP data leaving the printer will not be properly encrypted.
C. An MITM attack can reveal sensitive information.
D. An attacker can easily inject malicious code into the printer firmware.
E. Attackers can use the PCL protocol to bypass the firewall of client computers.
Correct Answer: B
QUESTION 5
A security administrator is tasked with conducting an assessment made to establish the baseline security posture of the
corporate IT infrastructure. The assessment must report actual flaws and weaknesses in the infrastructure. Due to the
expense of hiring outside consultants, the testing must be performed using in-house or cheaply available resources.
There cannot be a possibility of any requirement being damaged in the test.
Which of the following has the administrator been tasked to perform?
A. Risk transference
B. Penetration test
C. Threat assessment
D. Vulnerability assessment
Correct Answer: D
QUESTION 6
The availability of a system has been labeled as the highest priority. Which of the following should be focused on the
MOST to ensure the objective?
A. Authentication
B. HVAC
C. Full-disk encryption
D. File integrity checking
Correct Answer: B
QUESTION 7
The Chief Information Security Officer (CISO) in a company is working to maximize the protection efforts of sensitive
corporate data. The CISO implements a “100% shred” policy within the organization, with the intent to destroy any
documentation that is not actively in use in a way that it cannot be recovered or reassembled. Which of the following
attacks is this deterrent MOST likely to mitigate?
A. Dumpster diving
B. Whaling
C. Shoulder surfing
D. Vishing
Correct Answer: A
QUESTION 8
Joe, a security administrator, needs to extend the organization\\’s remote access functionality to be used by staff while
traveling. Joe needs to maintain separate access control functionalities for internal, external, and VOIP services. Which
of the following represents the BEST access technology for Joe to use?
A. RADIUS
B. TACACS+
C. Diameter
D. Kerberos
Correct Answer: B
QUESTION 9
After surfing the Internet, Joe, a user, woke up to find all his files were corrupted. His wallpaper was replaced by a message stating the files were encrypted and he needed to transfer money to a foreign country to recover them. Joe is
a victim of:
A. a keylogger
B. spyware
C. ransomware
D. a logic bomb
Correct Answer: C
QUESTION 10
A company is using a mobile device deployment model in which employees use their personal devices for work at their
own discretion. Some of the problems the company is encountering include the following:
1.
There is no standardization.
2.
Employees ask for reimbursement for their devices.
Employees do not replace their devices often enough to keep them running efficiently. The company does not have
enough control over the devices.
Which of the following is a deployment model that would help the company overcome these problems?
A. BYOD
B. VDI
C. COPE
D. CYOD
Correct Answer: D
QUESTION 11
A company was recently audited by a third party. The audit revealed the company\\’s network devices were transferring
files in the clear. Which of the following protocols should the company use to transfer files?
A. HTTPS
B. LDAPS
C. SCP
D. SNMPv3
Correct Answer: C
QUESTION 12
A company has three divisions, each with its own networks and services. The company decides to make its secure web
portal accessible to all employees utilizing their existing usernames and passwords. The security administrator has
elected to use SAML to support authentication. In this scenario, which of the following will occur when users try to
authenticate to the portal? (Select two.)
A. The portal will function as a service provider and request an authentication assertion.
B. The portal will function as an identity provider and issue an authentication assertion.
C. The portal will request an authentication ticket from each network that is transitively trusted.
D. The back-end networks will function as an identity provider and issue an authentication assertion.
E. The back-end networks will request authentication tickets from the portal, which will act as the third-party service
provider authentication store.
F. The back-end networks will verify the assertion token issued by the portal functioning as the identity provider.
Correct Answer: AB
QUESTION 13
In terms of encrypting data, which of the following is BEST described as a way to safeguard password data by adding
random data to it in storage?
A. Using salt
B. Using hash algorithms
C. Implementing the elliptical curve
D. Implementing PKI
Correct Answer: A
Latest leads4pass CompTIA dumps Discount Code 2020

About The leads4pass Dumps Advantage
leads4pass has 7 years of exam experience! A number of professional CompTIA exam experts! Update exam questions throughout the year! The most complete exam questions and answers! The safest buying experience! The greatest free sharing of exam practice questions and answers!
Our goal is to help more people pass the CompTIA exam! Exams are a part of life, but they are important! In the study, you need to sum up the study! Trust leads4pass to help you pass the exam 100%!
Summarize:
This blog shares the latest CompTIA SY0-501 exam dumps, SY0-501 exam questions and answers! SY0-501 pdf, SY0-501 exam video!
You can also practice the test online! leads4pass is the industry leader!
Select leads4pass SY0-501 exams Pass CompTIA SY0-501 exams “CompTIA Security+ Certification Exam”. Help you successfully pass the SY0-501 exam.
ps.
Get CompTIA Full Series Exam Dumps: https://www.fulldumps.com/?s=CompTIA (Updated daily)
Get leads4pass CompTIA Security+ exam dumps: https://www.leads4pass.com/comptia-security-.html
Latest update leads4pass SY0-501 exam dumps: https://www.leads4pass.com/sy0-501.html (1139 Q&As)
[Q1-Q12 PDF] Free CompTIA SY0-501 pdf dumps download from Google Drive: https://drive.google.com/file/d/1xQJKwWVvk_za8X5PTP1GorNuYmFyE039/